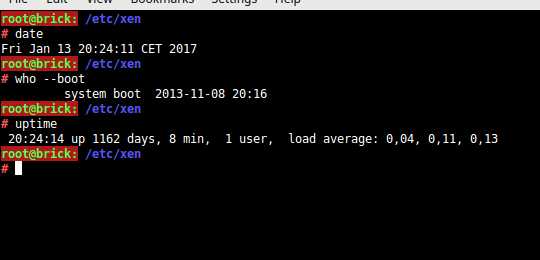
I replaced my server Brick yesterday, resetting my longest uptime on any machine ever. For the record:
Category: Technology (Page 7 of 48)
The Ubuntu page for reporting a bug does a good job of hiding the actual launchpad URL for filing a bug. Here is a direct one:
Windows 7 update service is slow to begin with, but trying it on a computer that has been off for a while is damn near impossible. This is a known issue, apparently.
You need KB3172605 to fix it.
Then supposedly, to make Windows Update faster, you can install KB2852386 to be able to remove old updates with the cleanup wizard. But, the option to remove unneeded Windows Update files never appeared for me.
Sources:
On my Multi Cycle bike, I have a SR Suntour CR9, serial number TF00478709, Series: CR, Year: 2015, Name: CR 9V-D-P-LO 700C TS 300/0, from 2015.
We found that if you do what the Apache documentation says and put quotes around the expr:
<RequireAny>
Require user victron
Require expr "%{REQUEST_URI} =~ m#^/.well-known/acme-challenge/.*#"
</RequireAny>
You get:
Cannot parse expression in require line: syntax error, unexpected $end
Remove the quotes around it…
As Bigsmoke indicated, we had some issues with google not finding content. For the same reason, I would like to share my insight into some stuff I write about:
Ytec, where I work since July 31 2015, is an IT company specializing in customer-specific custom software (“klantspecifieke maatwerk software“). Somewhere in late 2015, YTEC deployed a fancy new website based on React, which, to my surprise, is actually indexed somewhat decently by Google. Still, I want to be able to find my own posts on the YTEC blog when I filter by “site:blog.bigsmoke.us”, which is why I’m listing my posts there here:
- I contributed on a post about developing apps with React Native. Later, I might post some more about the pros and cons of using regular React in combination with Django.
- I wrote a post about the advantages of snapshot isolation, which was prompted by my being annoyed with all the problems caused by the Exact Globe ERP not supporting snapshot isolation for MS SQL Server.
When sending mail from a host behind NAT, you will run into trouble when the “From” says “root@host.localdomain”, because receiving servers will refuse that domain.
I’m not quite sure why, but setting myorigin used to be enough. Now I need to do this in main.cf:
# For when you have a host behind NAT that is refusing to # use hostname.realdomain.net as specified as origin. # You can test with: # postmap -q "fubar@hostname.somelocaldomain" regexp:/etc/postfix/sender_canonical sender_canonical_maps = regexp:/etc/postfix/sender_canonical
And in sender_canonical:
/^(.*@)host.*$/ ${1}hostname.realdomain.net
Or more generic:
/^(.*@.*\.)company$/ ${1}company.nl
And as usual, I use a relay host.
One of the inconveniences of encryption is the need to open the encrypted volume by hand when the computer/server boots. Luckily, you can easily automate that securely. You need a machine that will act as a key server, whether that’s a Raspberry Pi or some VPS you hire.
Take a server that will act as a key server and create a passwordless user:
adduser --disabled-password cryptsetupkeys su - cryptsetupkeys mkdir keys chmod go-rwx keys
We’re going to use ~/.ssh/authorized_keys to give access to the key to one public key, and only from one IP (to prevent someone stealing your computer from also auto-unlocking it):
from="2a01:1b0:5256:1:2:3:4:5",command="/usr/local/bin/catkey.sh keys/server1.key" ssh-rsa AAA...vJxw== root@server1 from="1.2.3.4",command="/usr/local/bin/catkey.sh keys/server2.key" ssh-rsa AAA...vJxw== root@server2
The /usr/local/bin/catkey.sh can be:
#!/bin/bash # # Script to be used as only permitted command to echo the key # data for cryptsetup encrypted partitions. # # from="1.2.3.4",command="/usr/local/bin/catkey.sh keys/server1.key" ssh-rsa AAA...vJxw== root@server2 # # http://blog.bigsmoke.us/2016/05/22/download-dmcrypt-cryptsetup-encryption-key-from-remote-server-and-auto-mount keyname="$1" keyfile="$HOME/$keyname" hostname="$(hostname)" mailto="you@example.com" mailfrom="Autokeydecryptor <you@example.com>" subject="Cryptsetup key access for '$keyname', '$USER' on '$hostname'" if [ -z "$keyname" ]; then message="key name not specified" echo "$message" echo "$message" | mail -a "From: $mailfrom" -s "$subject" "$mailto" exit 1 fi if [ ! -f "$keyfile" ]; then message="$keyfile not found or is not a regular file" echo "$message" echo "$message" | mail -a "From: $mailfrom" -s "$subject" "$mailto" exit 1 fi cat -- "$keyname" message="This is an audit of the access to cryptsetup keys on server '$hostname', account '${USER}', key '$keyname'. This should normally only happen on boot of the server which has the cryptsetup partition." echo "$message" | mail -a "From: $mailfrom" -s "$subject" "$mailto"
Then on the machine that has the encrypted volume, put the following in something like /etc/rc.local:
ssh -4 -o PasswordAuthentication=no "cryptsetupkeys@server.example.com" "dummy" | cryptsetup --key-file - luksOpen /dev/raidvg/mainencrypted maindecrypted # put the proper entry in /etc/fstab so this mount works mount /mnt/decryptedvolume
Or better yet put that in a separate script to be called from /etc/rc.local, because /etc/rc.local often has -e in the shebang, so it would stop on any error in that script, possibly failing to execute your command. Why that -e is there is a mystery to me, but that’s another story.
The less obvious flags explained:
-4is to make sure thefromclause will always work, also if your ISP suddenly gives you IPv6.-o PasswordAuthentication=nois necessary to be sure the command fails if the login fails. Otherwise, should your IP address change, the command may hang on password input (if it’s not smart enough to detect a non-interactive terminal).
I had a server that booted with a degraded array every time, because there was a USB drive attached to it, that messed up the auto detection. I solved it by putting this in mdadm.conf:
# This is to try to solve the problem that the array always boots as degraded when I boot the server with a USB disk attached. # http://serverfault.com/questions/722360/debian-server-has-degraded-mdam-array-on-every-boot/ DEVICE /dev/disk/by-id/ata-*
Then run:
update-initramfs -u
I still don’t know what went wrong, though. It can plainly see what drivse should be in the array.
Recent Comments