I’m learning Spanish from a Dutch method called Eso sí. Approaching chapter 10, I noticed that I would benefit from first learning the words introduced in each chapter before starting on the chapter’s text and exercises. From doing some exercises on Spanish learning websites (especially www.studyspanish.com), I noticed that flash cards can be a great help.
When I used to be behind a Linux terminal, there would always be an abundance of open source flash card software only one apt-get or emerge away. But, I’m behind a Windows terminal, so I thought I’d better try my luck with some on-line tool to make flash cards.
I first came by The Amazing Flash Card Machine.
I registered an account and created a few cards.

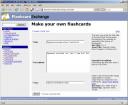
I didn’t find the process of adding cards in the Flash Card Machine very quick or supple, so I went to the next tool, FlashcardExchange.
Registering an account again was pretty straight-forward, except the the confirmation mail took ages to arrive, which made me click the resend confirmation link (which was very well presented) twice and even change my registration email address before I noticed all four mail had finally arrived when I returned to my desk after a few hours.
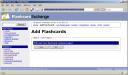
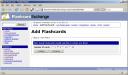
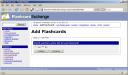
I created two card sets using their clean GUI. About that GUI: although clean, it takes a few too many steps to create a new card set or to start studying a card set:
They have the option to add the contents of multiple card sets to a single Leitner card file, but you then need to pay a one-time fee of $19.95. I’ve considered hashing out the 20 dollars, because the site has a clean design and offers good import/export features (a must if I’m going to shell out money for any service). However, with a GUI that gets in the way of adding cards, I’m going to keep the money where it is.
When I looked a little further, I noticed a pretty cool flashcard wiki anyone can edit, but again, no Leitner card files.
In the end I returned to open source desktop software again. Amazingly some of it supports Windows because the software is written in Java or because the developers feel my pain. Now, next time, I still have to choose between three fine applications.






![[Hacker glider button]](http://blog.bigsmoke.us/uploads/2009/01/hacker-emblem-80x15.png)
Recent Comments